Career
As cyber attacks and threats increase every day, interest and employment in the field of cybersecurity continue to grow. Companies invest in this field to protect their reliability and reputation, while countries also invest similarly to prepare for potential cyber warfare.
The increase in investments in cybersecurity drives both technological innovation and the expansion of job opportunities in the sector.
Below, you can see graphs showing employment numbers and workforce gaps in the cybersecurity sector.
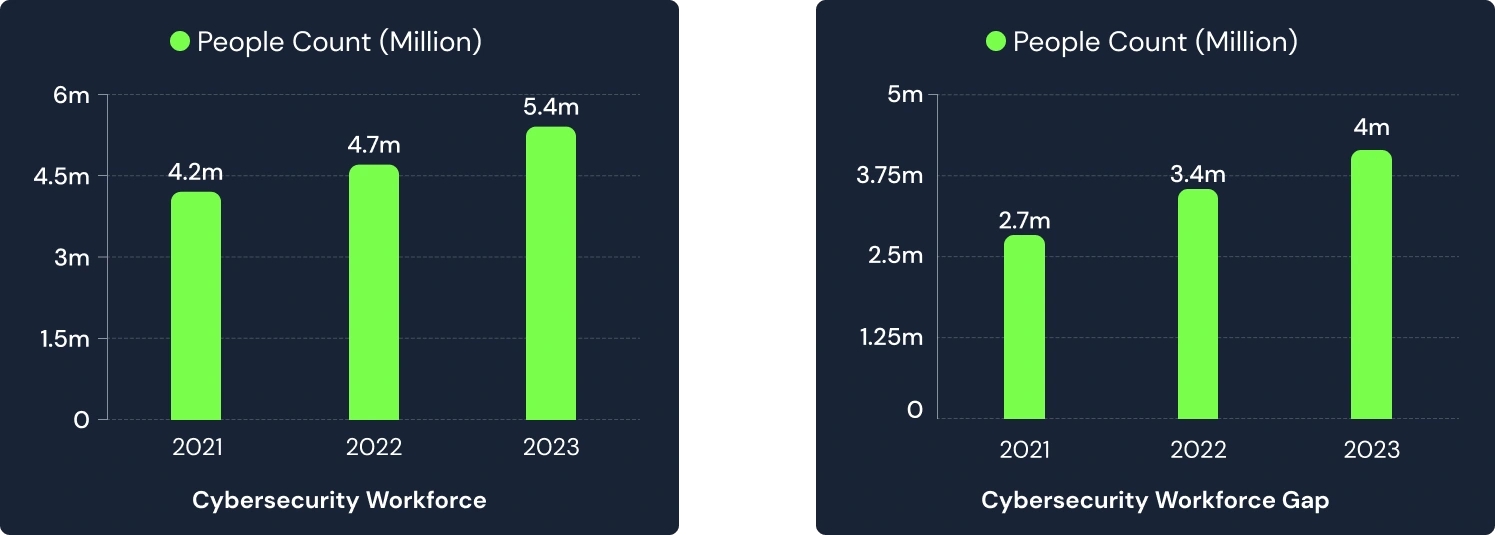
The data were obtained from (ISC)² (International Information System Security Certification Consortium) reports.
As seen in the above graphs, although there is an increasing employment rate in recent years, the workforce gap also grows each year.
Various positions in cybersecurity include developing defense and attack strategies, hardening systems to enhance security, or performing penetration tests to improve the security of institutions.
Career Journey
Anyone considering a career in cybersecurity will encounter many challenges and opportunities on this journey. The key to success in this process is undoubtedly regular and focused discipline.
Since cybersecurity requires deep technical knowledge, you may occasionally feel inadequate. However, aside from these challenges, the sector offers high financial rewards and flexible working conditions, such as remote work, making it an attractive field.
It is important to network and meet experienced professionals in this field to advance. Connecting with these individuals through online forums, professional networks like LinkedIn, Discord channels, or cybersecurity conferences and workshops can provide significant benefits in terms of knowledge exchange.
As you expand your network and enhance your technical skills, don't forget to develop your social skills, which are often overlooked but crucial for cybersecurity professionals. Communication skills, responsibility, team collaboration, and problem-solving abilities are among the essential social characteristics needed for success in this field.
As someone starting or considering starting a career in cybersecurity, you should ask yourself the following questions:
How strong is my interest in technology and innovation?
How open am I to learning new information?
Do I trust myself in solving problems I encounter?
Am I a team player?
How do I react under stress, and how can I manage it?
Am I ready to work long hours if needed to complete projects on time?
Cybersecurity is a constantly evolving field that presents new challenges. Therefore, you must be prepared for the challenges you will encounter and continually learn and adapt to succeed in your cybersecurity career.
Teams
Cybersecurity is a field with many sub-disciplines. The teams listed below help organizations counter cyber threats and ensure the organization's security. Although each team has different roles and responsibilities, they all serve a common goal: strengthening the organization's cybersecurity posture.
Red Team
The Red Team is a group that acts from the attacker's perspective to test an organization's cybersecurity. Their aim is to discover potential vulnerabilities and security gaps, exploit these weaknesses, and realistically test the organization's cyber defense capabilities. Red Team operations include various methods such as attack scenarios, penetration tests, and social engineering tactics. Their work helps understand how well the organization's defenses are prepared for real-world threats.
Blue Team
The Blue Team is responsible for strengthening and maintaining the organization's cybersecurity defenses. This team defends the organization against the Red Team's attack attempts, continuously monitors and improves security measures to prevent and detect security breaches. The Blue Team's duties include monitoring and managing firewalls, intrusion detection systems, and other security solutions, incident response, implementing security policies, and providing security awareness training to employees.
Purple Team
The Purple Team aims to maximize the organization's cybersecurity capabilities by combining the efforts of the Red and Blue teams. Serving as a bridge between the Red and Blue teams, the Purple Team allows both sides to learn from each other and develop their skills. They guide the Blue Team on how to address vulnerabilities discovered by the Red Team and provide feedback to enhance the effectiveness of defense strategies.
Bug Bounty
Bug Bounty is a defense strategy for companies and a revenue source for cybersecurity researchers that has gained significant popularity in recent years. In bug bounty programs, cybersecurity researchers who discover security vulnerabilities within the specified scope and report these vulnerabilities are rewarded with money. Through these programs, organizations become more resilient to cyber attacks while cybersecurity researchers can earn income
Last updated