Symmetric Encryption
Symmetric encryption is a method of encryption where the same key is used for both encryption and decryption. In this method, both the sender and the receiver share a secret key, which is used to encrypt and decrypt the data. Symmetric encryption is fast and efficient but can face challenges in key distribution and management.
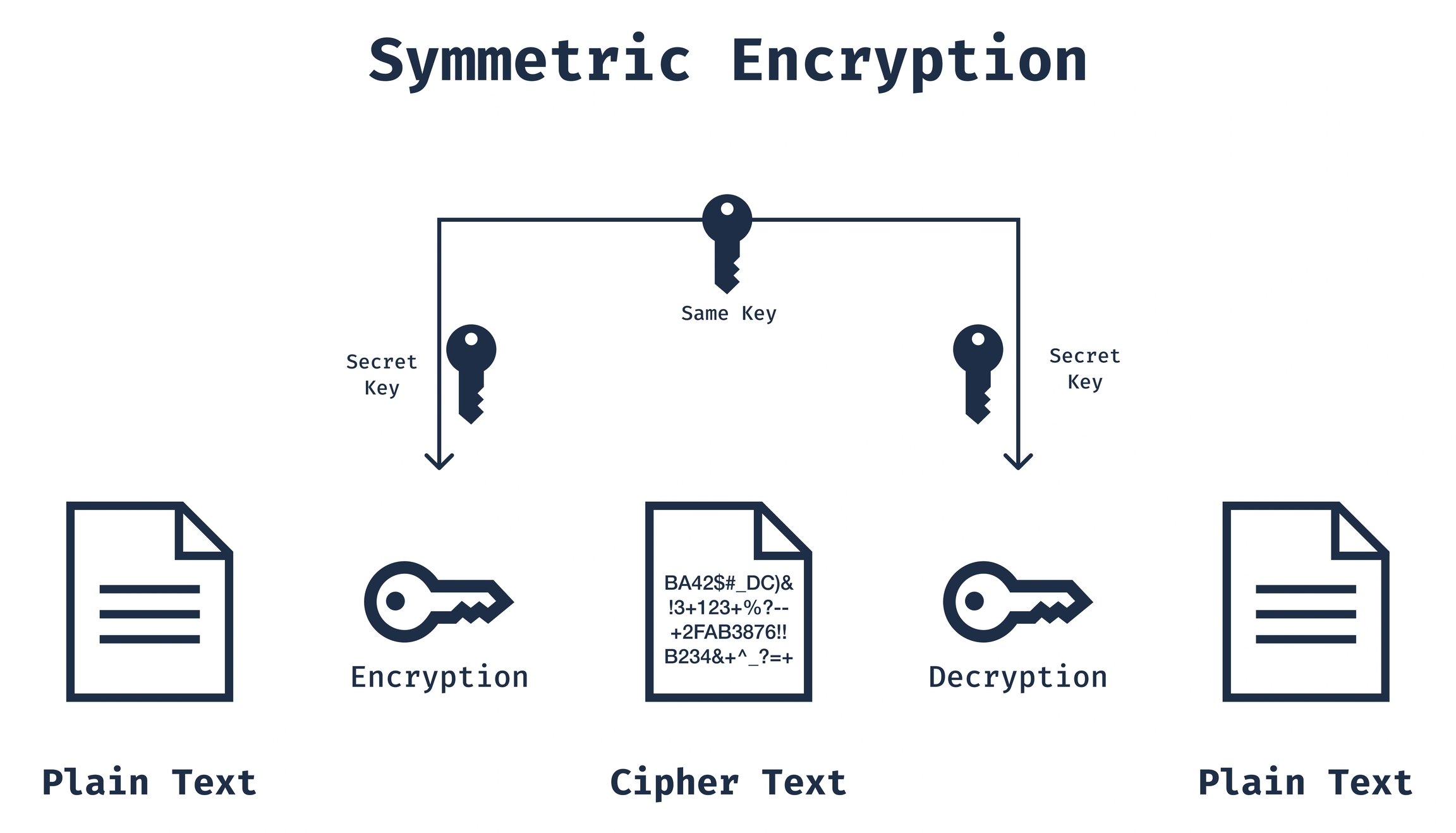
Symmetric Encryption Algorithms
Symmetric encryption algorithms can be categorized into two main types: block ciphers and stream ciphers.
Block Ciphers
Block ciphers process data in fixed-size blocks, performing encryption and decryption operations on each block using a specific algorithm and key.
1. DES (Data Encryption Standard)
Developed by IBM in the 1970s and accepted as a standard by the U.S. government in 1977.
Uses a 56-bit key length.
It is no longer widely used due to insufficient security.
2. 3DES (Triple DES)
Developed to address the security weaknesses of DES.
Performs encryption using DES three times (encrypt-decrypt-encrypt).
Uses a 168-bit key length.
3. AES (Advanced Encryption Standard)
Accepted as a standard by NIST (National Institute of Standards and Technology) in 2001.
Supports key lengths of 128, 192, and 256 bits.
It is widely used due to its security and speed.
Stream Ciphers
Stream ciphers process data as a stream of bits or bytes, performing encryption and decryption operations on the data stream. This method is especially suitable for encrypting data streams.
1. RC4 (Rivest Cipher 4)
Developed by Ron Rivest in 1987.
Has a variable key length.
Though it is fast and simple, it has some security weaknesses.
2. Salsa20 and ChaCha20
Secure and fast stream ciphers.
Preferred in environments requiring low power consumption, such as mobile and IoT devices.
Advantages and Disadvantages of Symmetric Encryption
Advantages
Speed: Symmetric encryption algorithms are much faster than asymmetric encryption algorithms.
Efficiency: Requires fewer computational resources.
Simplicity: Algorithms and implementations are generally simpler.
Disadvantages
Key Distribution: Securely sharing and distributing the key can be challenging.
Key Management: Managing a large number of keys can be complex, especially in large networks.
Security: If the key is compromised, all encrypted data is at risk.
Block Cipher Modes of Operation
Block ciphers can be operated in different modes to enhance security and performance.
1. ECB (Electronic Codebook) Mode
Each block is encrypted independently.
Identical plaintext blocks produce identical ciphertext blocks.
Not secure due to risks of pattern repetition.
2. CBC (Cipher Block Chaining) Mode
Each block is XORed with the previous ciphertext block before encryption.
An initialization vector (IV) is used for the first block.
More secure by eliminating patterns.
3. CFB (Cipher Feedback) Mode
The encryption algorithm functions like a stream cipher.
Plaintext blocks are XORed with the ciphertext.
4. OFB (Output Feedback) Mode
The encryption algorithm functions like a stream cipher.
Ciphertext blocks are XORed with plaintext blocks.
5. CTR (Counter) Mode
A counter value is used for each block's encryption.
Blocks can be processed in parallel, improving performance.
Applications
Symmetric encryption is used in various areas for secure data transmission and storage.
Data Storage: File and disk encryption
Communication: VPN and SSL/TLS protocols
Authentication: Key management systems
Last updated